Select The Term That Best Describes Automated Attack Software?
Select the term that best describes automated attack software?. OWASP is a nonprofit foundation that works to improve the security of software. A DDoS attack is also an attack on systems resources but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker. Audit logs from a small companyגs vulnerability scanning software show the following findings.
Select the term that best describes automated attack software. Destinations scanned-Server001- Internal human resources payroll server-Server101-Internet-facing web server-Server201- SQL server for Server101-Server301-Jumpbox used by systems administrators accessible from the internal network. Unlike attacks that are designed to enable the attacker to gain or increase access denial-of-service doesnt provide direct benefits for attackers.
An entity that has value. Experimenting with automated attack or counterattack tools is likely to be a fairly dicey proposition potentially leading to a trip to prison even when we have the best intention. What are some of the drawbacks to using HIDS instead of NIDS on a server.
Select the two best answers A. Packets are captured the pertinent information is extracted and then packets are placed back on the network. Select the information protection item that ensures that information is correct and that no unauthorized person or malicious software has altered that data.
A HIDS has a low level of detection of operating system attacks. Matt Bishop and Dave Bailey 13 give the following definition of computer vulnerability. An attacker takes advantage of the addgrace period to monopolize names without ever paying for them.
Attacks on the main website for The OWASP Foundation. Which of the following is the term used to describe the method of gaining unauthorized access to a computer system in which attackers use an automated process to guess a system users passwords. Select the term that best describes automated attack software.
Targeted attacks against financial networks unauthorized access to information and the theft of personal information. The attack or harmful event or the opportunity available to a threat agent to mount that attack.
A computer system is composed of states describing the current configuration of the entities that make up the computer system.
Matt Bishop and Dave Bailey 13 give the following definition of computer vulnerability. CCNA Cybersecurity Operations Version 11 - CyberOps Chapter 6 Exam Answers full pdf free download new question 2019-2020 100 scored. Audit logs from a small companyגs vulnerability scanning software show the following findings. The attack or harmful event or the opportunity available to a threat agent to mount that attack. OWASP is a nonprofit foundation that works to improve the security of software. Select the term that best describes automated attack software. Successful attacks are usually not from software that is poorly designed and has architecturedesign weaknesses. What is the significant characteristic of worm malware. A worm can execute independently of the host system.
Select the term that best describes automated attack software. Audit logs from a small companyגs vulnerability scanning software show the following findings. A DDoS attack is also an attack on systems resources but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker. Advanced persistent threat what class of attacks use innovative attack tools and once a system is infected it silently extracts data over an extended period. A HIDS cannot detect network attacks. In many countries such tools operating outside of a very controlled environment will likely violate a variety of laws. Which of the following best describes a DDoS attack.






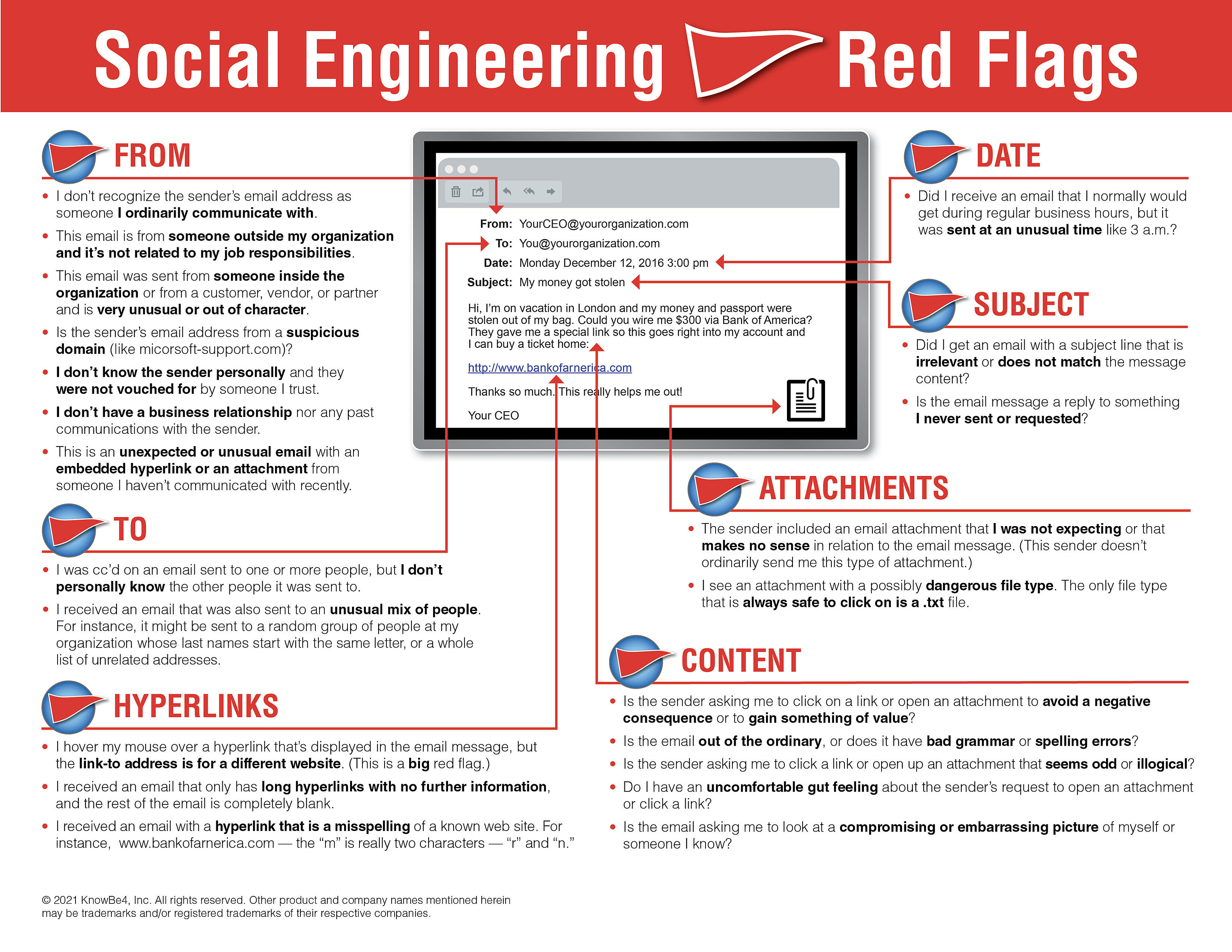










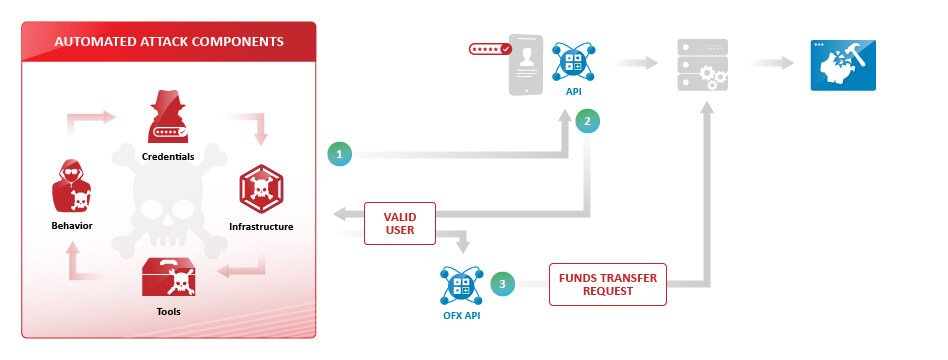
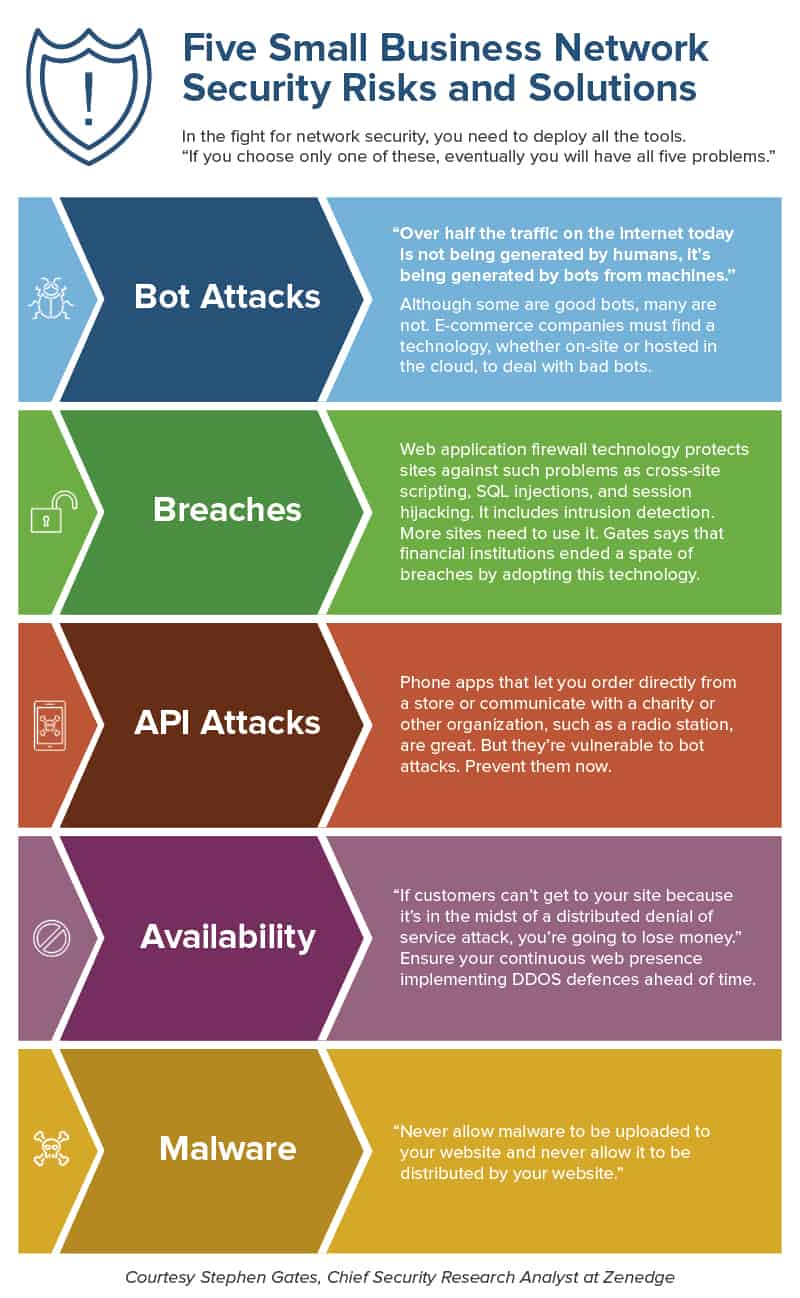




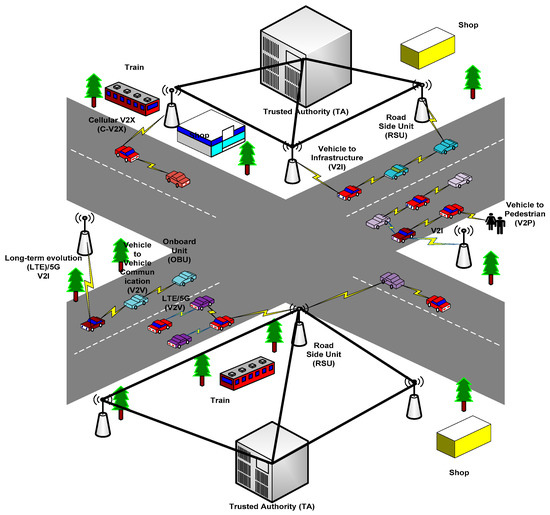


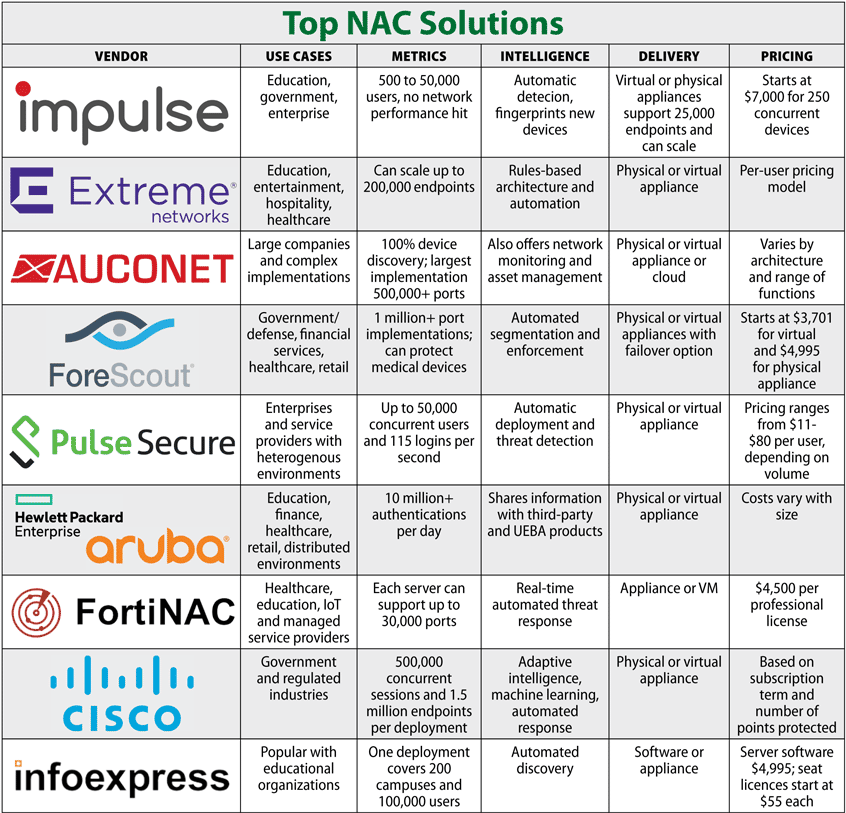
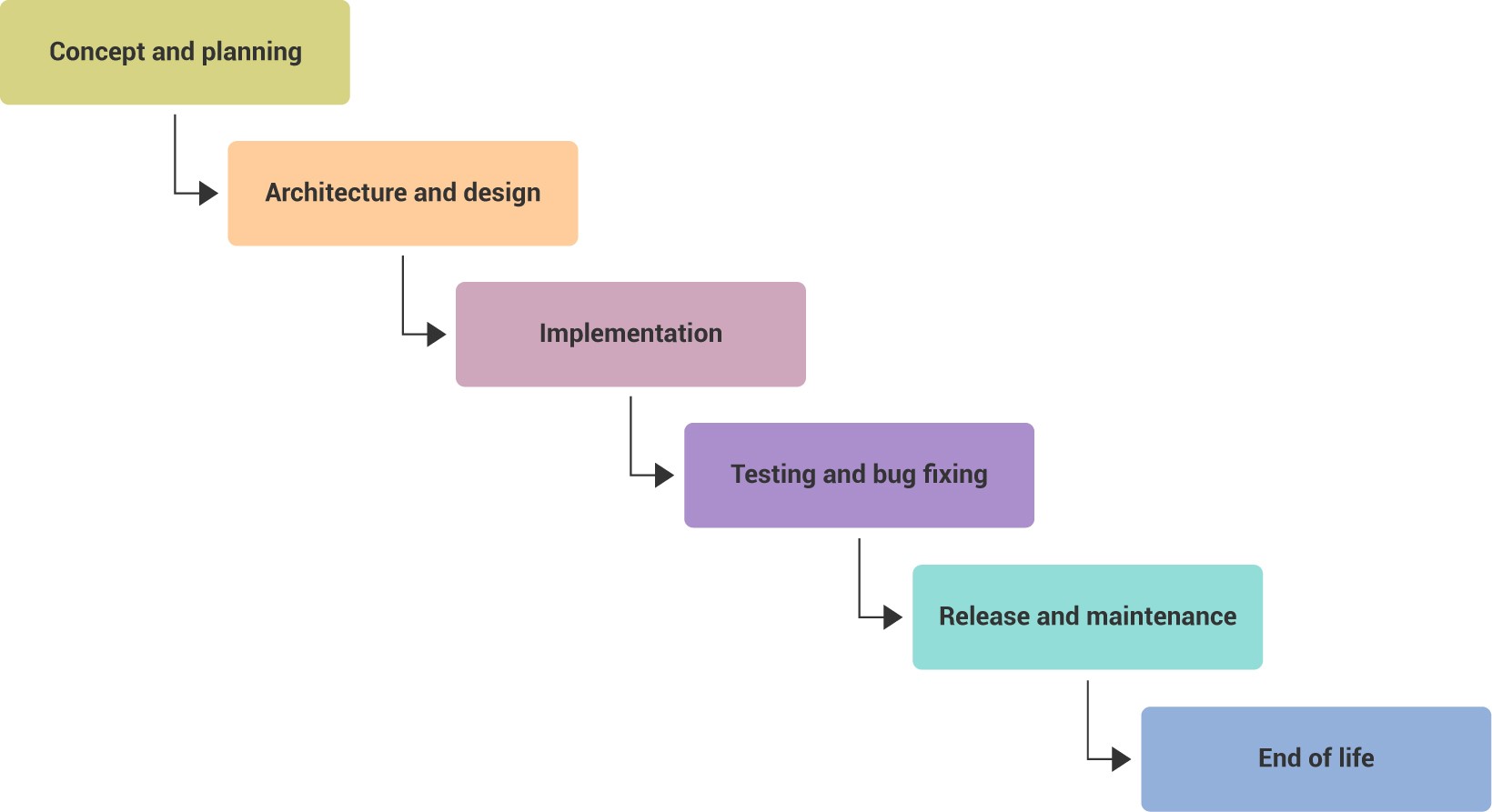


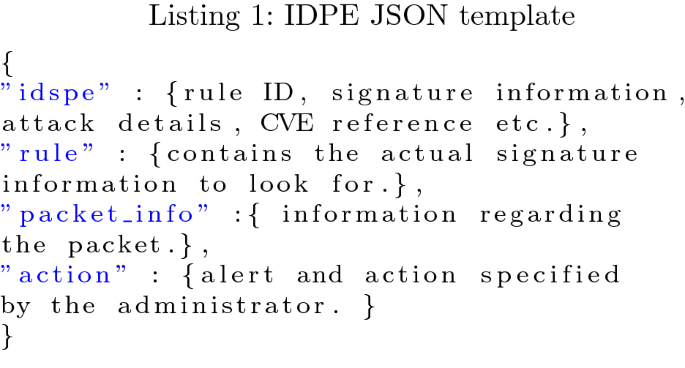



Post a Comment for "Select The Term That Best Describes Automated Attack Software?"